Tips: Enhancing Remote Utilities Security
In this blog post you will learn about optional security features that you can enable to add another layer of protection to your Remote Utilities installation.
Remote Utilities default security settings are strong enough to satisfy even the strictest requirements. With its persistent end-to-end data transfer encryption and certificate-based Host and Server identity verification the program protects your remote transfer data from unauthorized access and warns you if your remote modules are tampered with. Besides, you must enable at least one authorization method and enter access credentials in order to log in (authorize) on a remote Host.
But what about other security features which are not enabled by default? Further reinforcing your already strong and impregnable fortress will never hurt after all. Continue reading below to learn how to turn on additional layers of protection.
Enable two-factor authentication
You must always use strong access passwords for your remote Hosts. However, in a scenario where your passwords are guessed or stolen by hackers the two-factor authentication (2FA) can be your safety net and the last line of defense that can protect your Hosts even if your passwords are compromised.
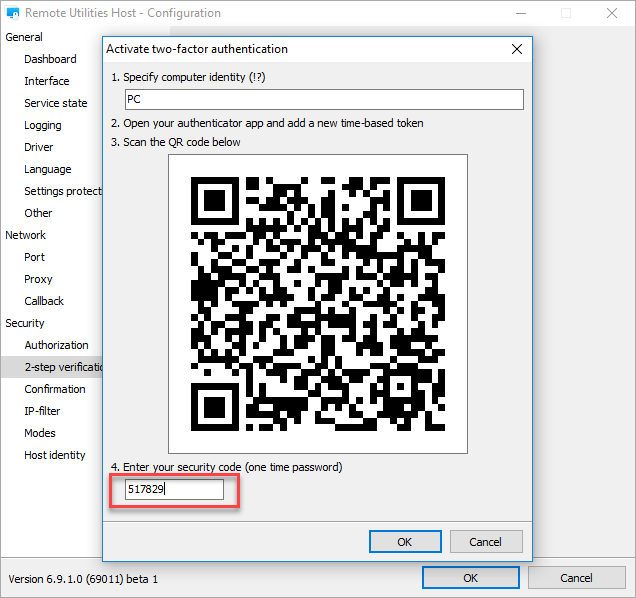
2FA works with any Host authorization method. Google Authenticator or a similar smartphone app is required to receive the OTPs (one-time passwords). You can either manually enable 2FA in Host settings after it has been installed or pre-configure your Host installer in the MSI Configurator.
Encrypt your address book
You can encrypt your address book so that a passphrase will be required to unlock the Viewer interface each time you start the program.
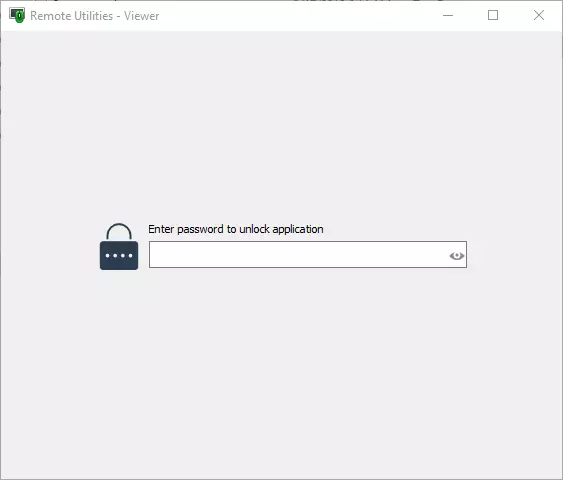
Whenever you are travelling with your Viewer laptop or use the portable Viewer off a USB stick address book encryption will help you protect your address book data on a local or USB drive.
Learn how to enable address book encryption
Password-protect Host settings
If you are an admin who remotely supports company employees, you might want to protect Host settings from change by the remote user. As with other Host settings you can either manually enable this option on each Host or enable it during MSI Configuration of your Host installer.
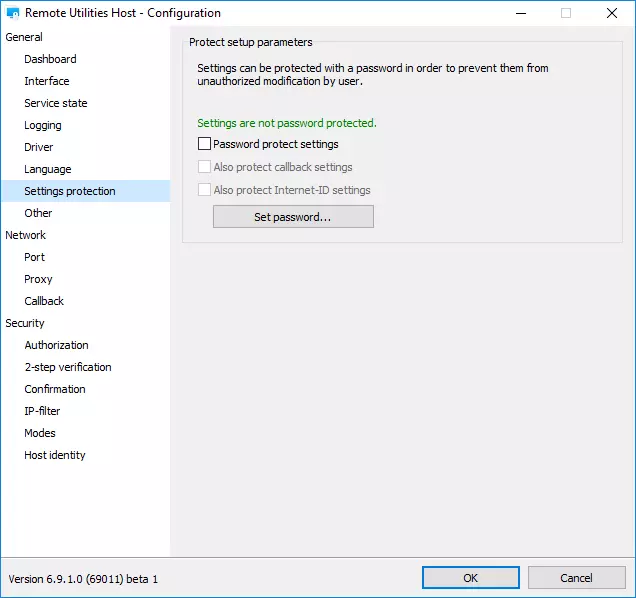
Learn how to enable Host settings protection
Enable IP filtering
This is an often-overlooked feature that allows you to effectively protect your Host installations against unauthorized access even before authorization attempts and password guessing take place. IP filtering is available for Host and RU Server.
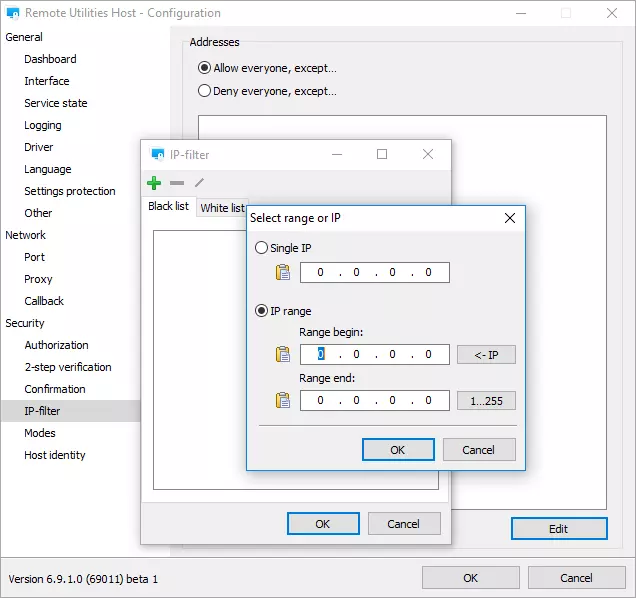
IP filtering uses a white list and a black list. Use the white list to explicitly allow certain IP addresses and IP address ranges while filtering out all other IP addresses. Conversely, use the black list to block specific IP addresses from accessing your Host and allow all other IP addresses not included in the blocked range.
Learn how to use IP filter on the Host
Enable “Ask user permission”
The “Ask user permission” feature is designed to help protect the privacy of remote users. With this option enabled the remote user can decide whether to allow or deny and incoming remote connection.
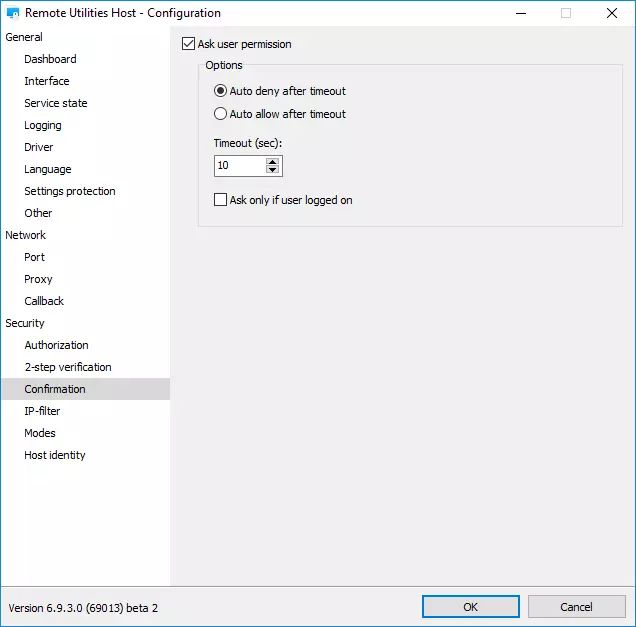
If your organization follows strict privacy rules we recommend that you enable this feature so that the people whom you support are not taken by surprise with your remote session.
Learn how to enable Ask User Permission
Conclusion
Your data transferred over the network as well as your program integrity are already well protected by the persistent security features. However, enabling the options above will add to your already secure setup and minimize if not eliminate the chance that your systems are compromised due to stolen passwords or address books. You may find these features especially useful if you want your configuration to conform to strict security regulations in your organization.
Image by vishnu vijayan from Pixabay