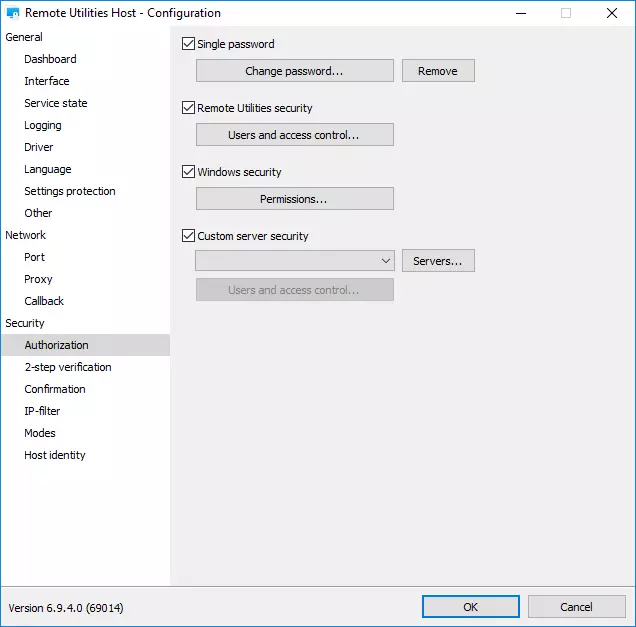
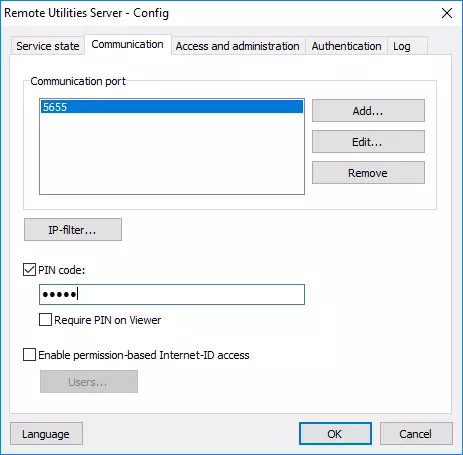
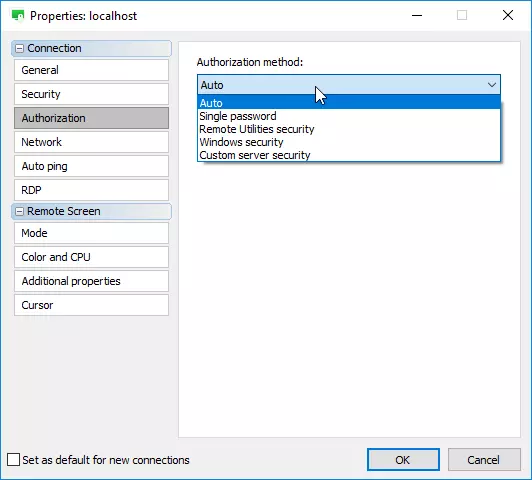
Remote Utilities 7.7.3.0 — What’s New
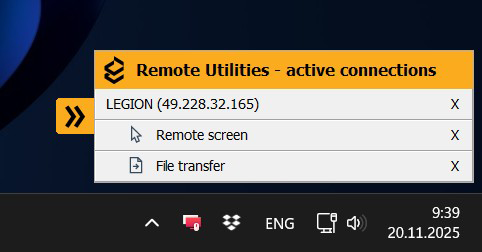
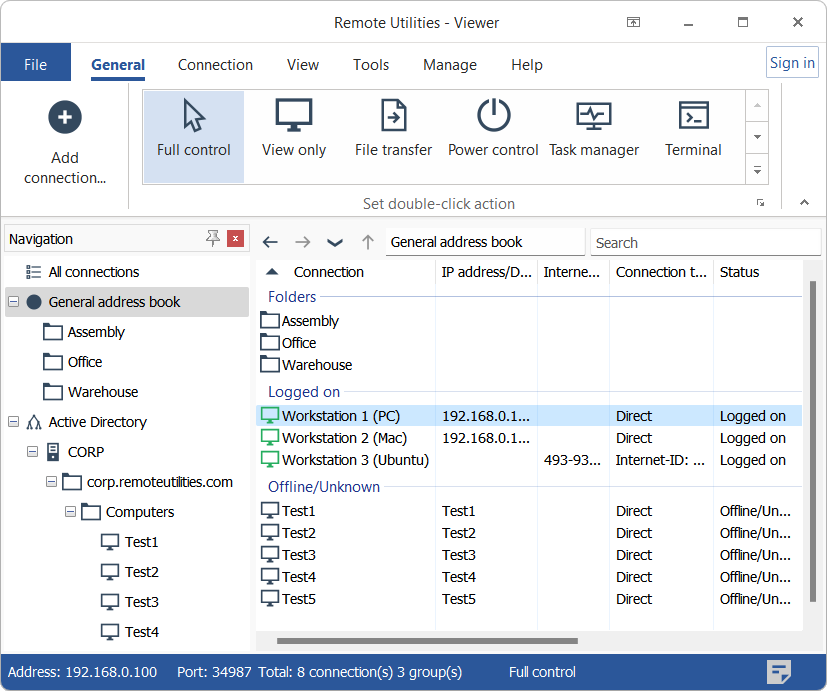
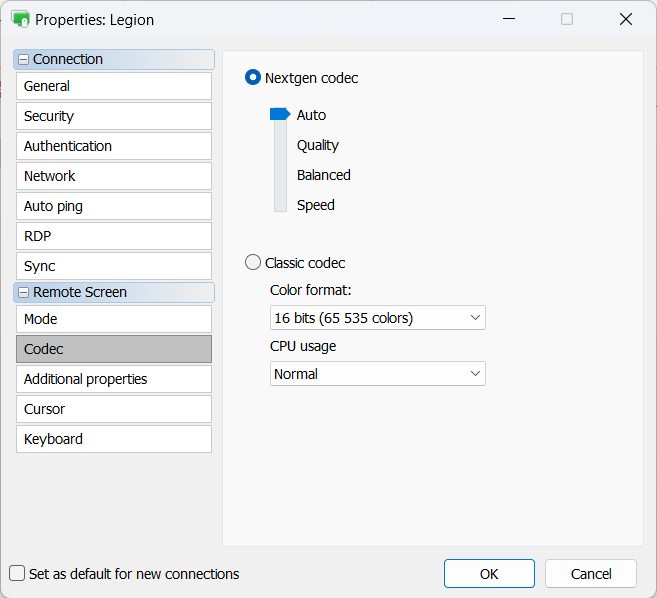
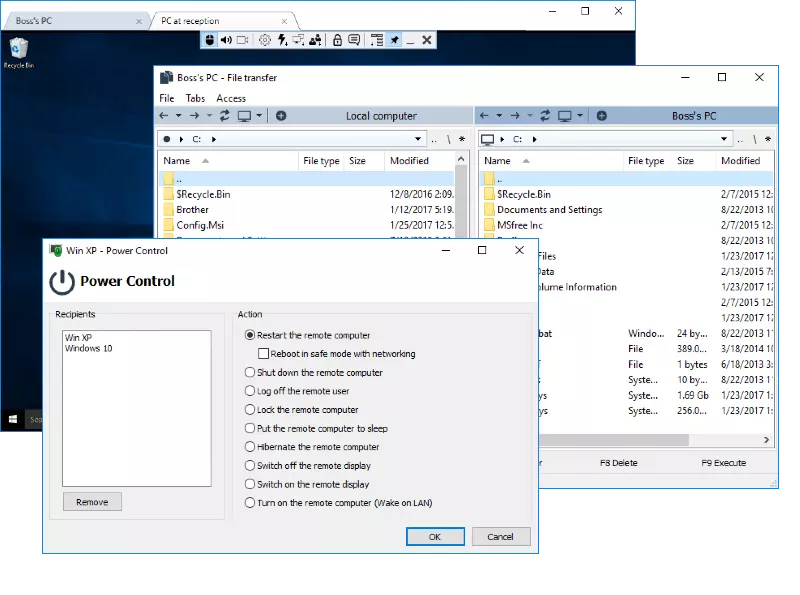
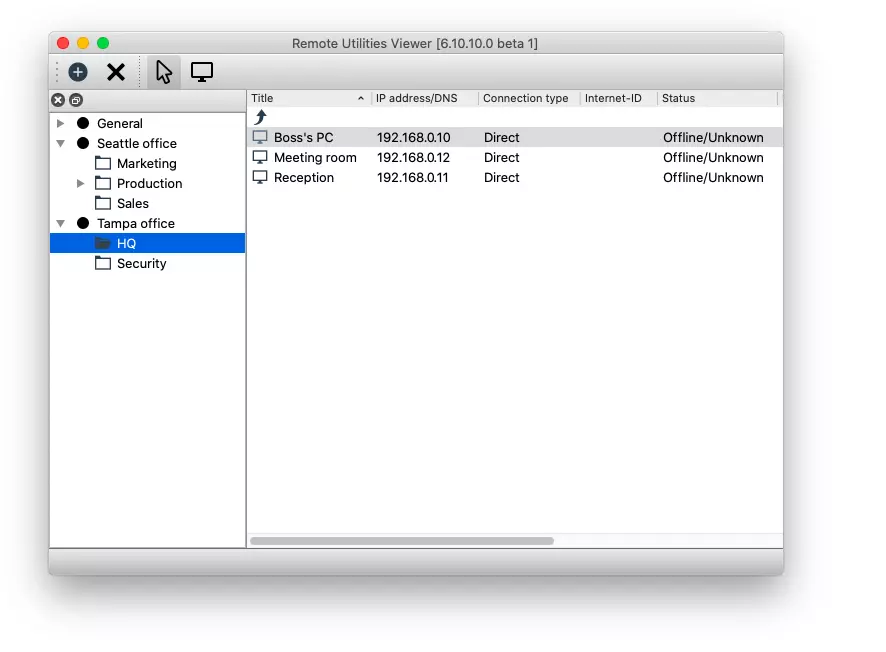
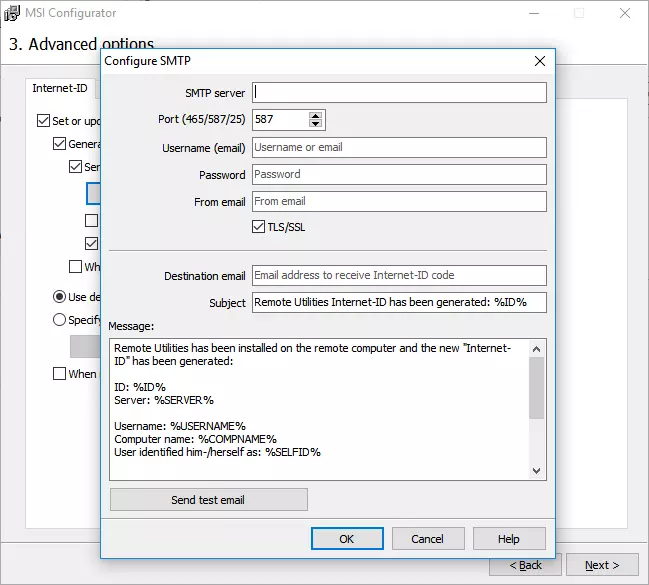
Remote Utilities 7.7.3.0 brings several improvements focused on security, transparency, and easier administration. This update introduces a smarter connection panel, more informative tray indicators, enhanced authorization features, and new tools to help admins manage Hosts and Servers more efficiently.