An Introductory Road Map to IPv4 and IPv6 Addresses
IP addresses are like the street addresses of the internet, crucial for ensuring information finds its way to the right place. With the transition from IPv4 to the newer IPv6, we're stepping into a new era of internet technology. This post will break down these concepts in a way that's easy to grasp, whether you're a tech enthusiast or just curious about how the internet works. Let's explore the fascinating world of IP addresses together.
Understanding IP Addresses
Networking has been integral to computing from the early days. Initially, connecting small networks was straightforward, using wires and simple protocols—rules ensuring data transmission.
As networks expanded, the need for a more robust, fail-safe protocol emerged. This led to the development of the TCP/IP protocol suite, with its first version released in 1981. Remarkably, it has remained largely unchanged, becoming the cornerstone of internet communication.
TCP/IP outlines how computers should exchange data to ensure swift, secure transmission. A crucial component of this is the IP address, a unique identifier for each device in a network, adhering to a specific format.
Diving into IPv4
When we mention "IPv4," we're referring to the original IP address format defined in the foundational TCP/IP protocols. According to the TCP/IP protocol suite, an IP address in the IPv4 format must utilize 32 bits (or four bytes). This format is familiar to anyone who has used the internet and the World Wide Web over the last 30 years, typically resembling:
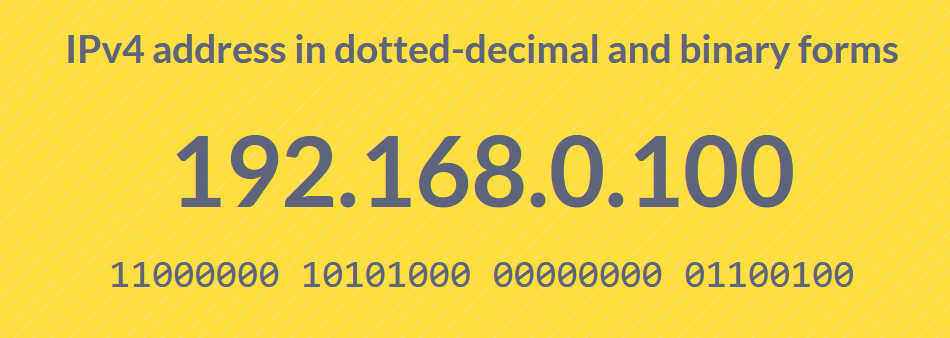
The binary sequence, consisting of 1s and 0s, represents how data is transmitted between computers. With a 32-bit limit, the maximum number of unique IPv4 addresses is around 4.3 billion (2^32).
Given the exponential growth in devices connecting to the internet, one might wonder why the network infrastructure hasn't faced collapse due to address exhaustion. The following section on NAT and routing will shed light on this.
The Use of NAT and Routing
How is it possible for the Internet to support connectivity for more than 4 billion devices when the IPv4 address space doesn't allow for that many unique addresses?
Enter NAT (Network Address Translation). NAT addresses this limitation with a straightforward solution: it enables entire networks to access the Internet through a single point, known as a router. Routers partition the network into segments, and communication across these segments is facilitated exclusively through the router. Each router connected to the Internet is assigned a unique IPv4 address (the public IP address).
Internally, the router uses a separate set of IP addresses to communicate with devices on the local network. This approach allows NAT to recycle IP addresses within a local network. Certain ranges of IP addresses, like 192.168.x.x, are reserved exclusively for local network use and are never exposed directly to the Internet.
An additional benefit of using routers is the enhancement of network security. Acting as gatekeepers, routers employ their integrated firewalls to filter out malicious requests, effectively protecting the devices within the network.
Specific IP Reservations
Regardless of the IP version or computer in use, certain IP addresses are universally reserved for specific functions, much like emergency and information services (such as 911 or 411) in telephony. For example, the IP address 255.255.255.255 is set aside for network-wide broadcasts, allowing messages to reach all devices on your network—ideal for disseminating critical information to employees. Similarly, the loopback address 127.0.0.1 enables a computer to refer to itself, even without a uniquely assigned IP, facilitating internal testing and communication. These reserved addresses also include concepts like subnets, enhancing network organization and security.
Subnets
Subnets allow for the creation of smaller, more manageable networks within a larger network, connected through a router. This segmentation enables precise control over access to certain resources, making it possible to grant specific file access to IT staff while limiting it for others. A subnet consists of a sequential range of IP addresses. Establishing a subnet is as straightforward as assigning IP addresses from a predetermined range to each device within the desired network segment. This approach enables the restriction of network segments, ensuring they are accessible only to devices within the subnet, thereby enhancing security and efficiency.
The Advent of IPv6
With the depletion of IPv4 addresses, the introduction of IPv6 has marked a significant milestone in internet technology. IPv6 employs a 128-bit address format, which greatly expands the pool of available addresses. This vast address space removes the need for Network Address Translation (NAT), permitting each device to have its own unique global IP address. This simplification of network configurations enhances end-to-end connectivity.
IPv6 addresses are composed of eight groups, each separated by colons. Each group represents a hexadecimal number (a number in the base-16 system). For instance:

Given the 128-bit length of an IP address, the number of possible combinations increases dramatically, far surpassing the quantity of addresses that will likely ever be needed. However, the expansion of the IP address space is not the sole rationale behind the introduction of IPv6. IPv6 also introduces enhanced security features, more efficient routing, and improved support for mobile devices, thereby making the internet more reliable and accessible.
The State of IPv6 Adoption
Google consistently monitors the prevalence of IPv6 connectivity among its users. Current data indicates that approximately 45% of Google users connect to Google servers using IPv6.
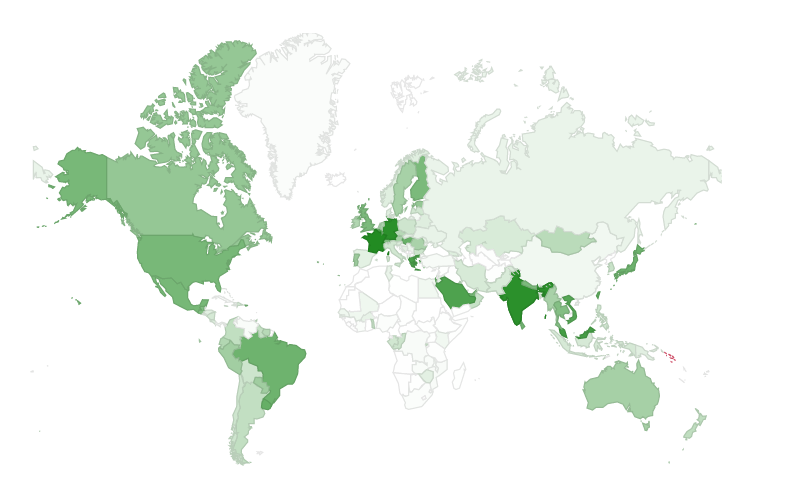
In addition to global statistics, Google also tracks IPv6 adoption by country. France, Germany, India, and Saudi Arabia lead in IPv6 deployment, each nearing 75% adoption, with several other nations not far behind.
IPv6 and Remote Utilities
Remote Utilities' remote desktop software aligns with the global trend towards IPv6 adoption. The protocol is currently supported for direct connections and will soon be available for both hosted and self-hosted Internet-ID connections. Stay tuned for updates!
Conclusion
In simple terms, moving from IPv4 to IPv6 is a big step forward for the internet. It solves the problem of running out of IP addresses and makes the internet more secure and easier to use. With IPv6, every device can have its own unique address, making connections simpler and more direct. Companies like Google are keeping an eye on how many people are using IPv6, and it's becoming more common around the world. Tools like Remote Utilities are also updating to use IPv6, showing that the future of the internet is heading in this direction.
Last updated: