Version 6.9: PIN-code + Rerun Agent as
Remote Utilities 6.9 Beta 2 has been released. We added PIN-code protection for Internet-ID connection when used with the self-hosted server, the ability to remotely restart the Agent as administrator and a few other features and bugfixes. See this post for details.
PIN-code protection for Internet-ID
This is related to your use of the self-hosted server for Internet-ID connection.
Problem
Previously, anyone who knew your server address and port could use your server to broker an Internet-ID connection for their own Viewer and Host the same way you did for yours. This could result in unidentifiable Hosts hanging in the "Idle" and "Active" tabs in the server Admin Console. While not a security vulnerability per se, it was still an annoyance.
One way to prevent unauthorized Hosts from connecting to your server is to use IP filtering set up through the server configuration window. However, this method isn't flexible enough to be used in every situation. Sometimes you don't know from what IP address a remote Host will be connecting to your server, and even if you did it would take unnecessary time and effort to keep track of these IP addresses and adding them to your IP filter table.
Solution
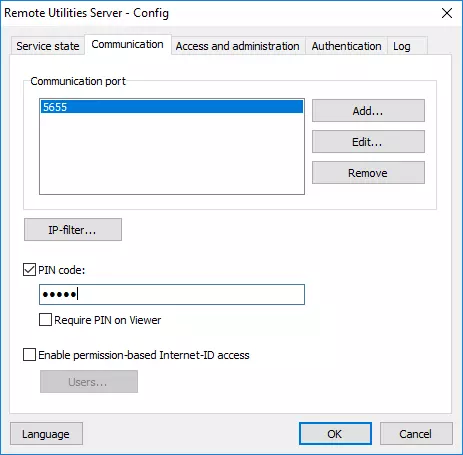
Now you can create a special "PIN" (password), that the server would ask any "incoming" Host before letting it use this server as an intermediary for Internet-ID connection. The PIN is set in the server configuration window:
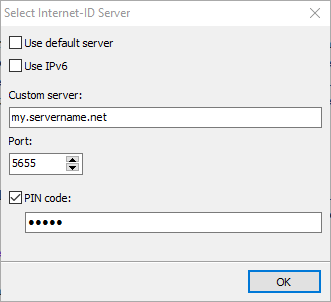
On the Host side the same PIN must be entered in the Internet-ID connection settings dialog:
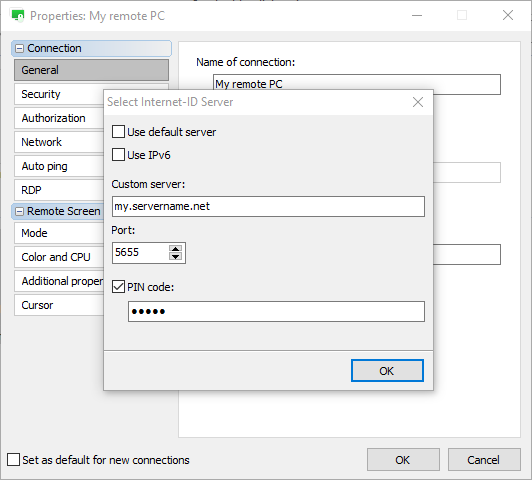
You can also enable PIN for the Viewer. In this case you should select the "Require PIN on Viewer" check box and enter the PIN in connection properties for each remote connection that uses the server:
Using the PIN on the Viewer side may be overkill but you can still enable it if you think it is necessary. Just do not forget to specify the PIN in the connection properties as shown above or you will not be able to connect to a server if it has a PIN set and "Requre PIN on Viewer" checkbox enabled.
Restricting Internet-ID use to specific accounts
Yet another way to limit the use of the server's Internet-ID feature is enabling permission-based access to Internet-ID. You can select "Enable permission-based Internet-ID access" and restrict the use of the Internet-ID to specific server accounts (you must create them first).
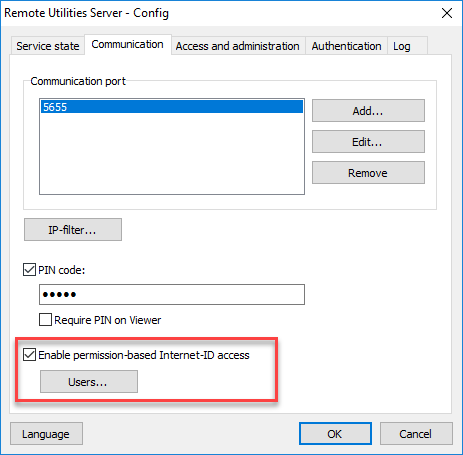
This feature works independently from the PIN feature above. Both features can work side by side and complement each other. Essentially, they use different criteria for restriction — the PIN feature allows or denies access based on Host whereas the permission-based access feature allows or denies access based on user account.
Remotely restarting Agent as administrator
Now you can remotely restart Agent as administrator in order to be able to control the UAC prompt on the remote computer. This feature is useful when the remote user is logged in as standard Windows user and you need to perform actions that require administrative privileges, such as installing software.
With Host you can control UAC prompts right away. However, Host requires administrative privileges to install. Besides, there may be other reasons why you use Agent instead of Host, such as spontaneous and/or one-time remote support. Using Host for this scenario would be overkill.
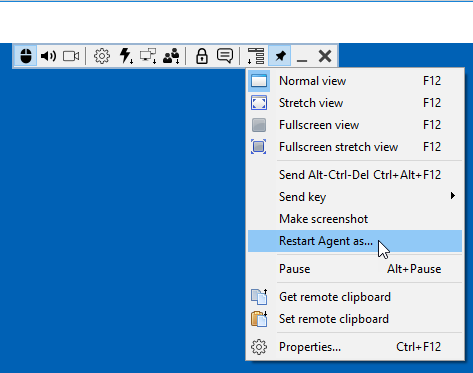
When you are being connected to a remote Agent which is run as a standard non-admin Windows user (a common scenario), there is a new item "Restart Agent as" in the Addional Commands menu on the Full Control mode toolbar:
You must provide user credentials in the prompt window:
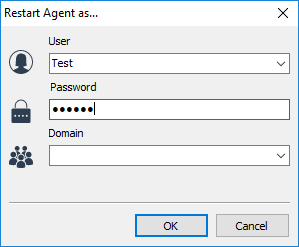
Click OK and the remote Agent will restart, this time as the user whose credentials you entered. In most cases you will use admin credentials in order to perform tasks that require elevated privileges.
If you have any questions or suggestions feel free to post in the community discussion.