Pros and Cons of Windows Remote Desktop Services
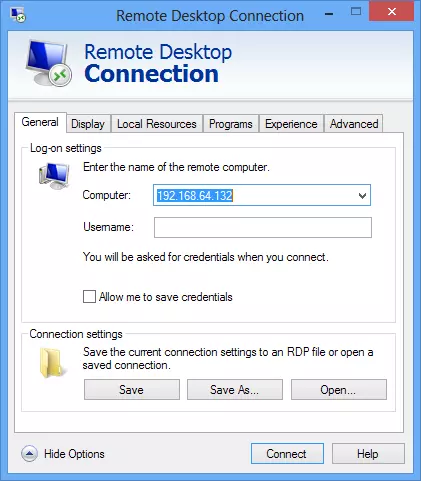
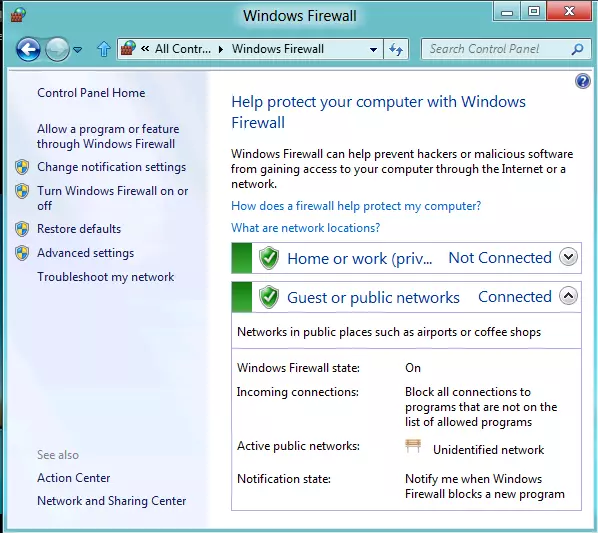
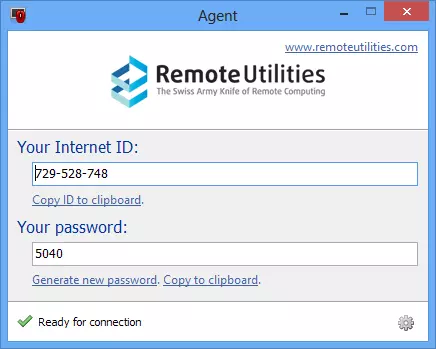
The Windows Remote Desktop Services, or Windows RDS for short, is Microsoft's remote desktop tool which is customized specifically to the features of Windows in all its various iterations. This service is available in both Windows 7 and Windows 8, and offers a free way to access a Windows computer remotely. Remote Utilities also supports RDP connection.