The Superiority of Decentralized Remote Access Over SaaS Models
Recent incidents involving security breaches in popular Software as a Service (SaaS) remote desktop tools have brought to light the inherent vulnerabilities associated with centralized, web-based services. This article delves into the risks posed by SaaS remote desktop solutions and presents a compelling case for decentralized alternatives, with a spotlight on Remote Utilities as a paradigm of security and autonomy in remote access.
The allure of SaaS-based remote desktop solutions lies in their convenience and ease of deployment. However, beneath the surface of these cloud-powered tools lie several significant risks that can jeopardize the integrity, privacy, and financial stability of organizations.
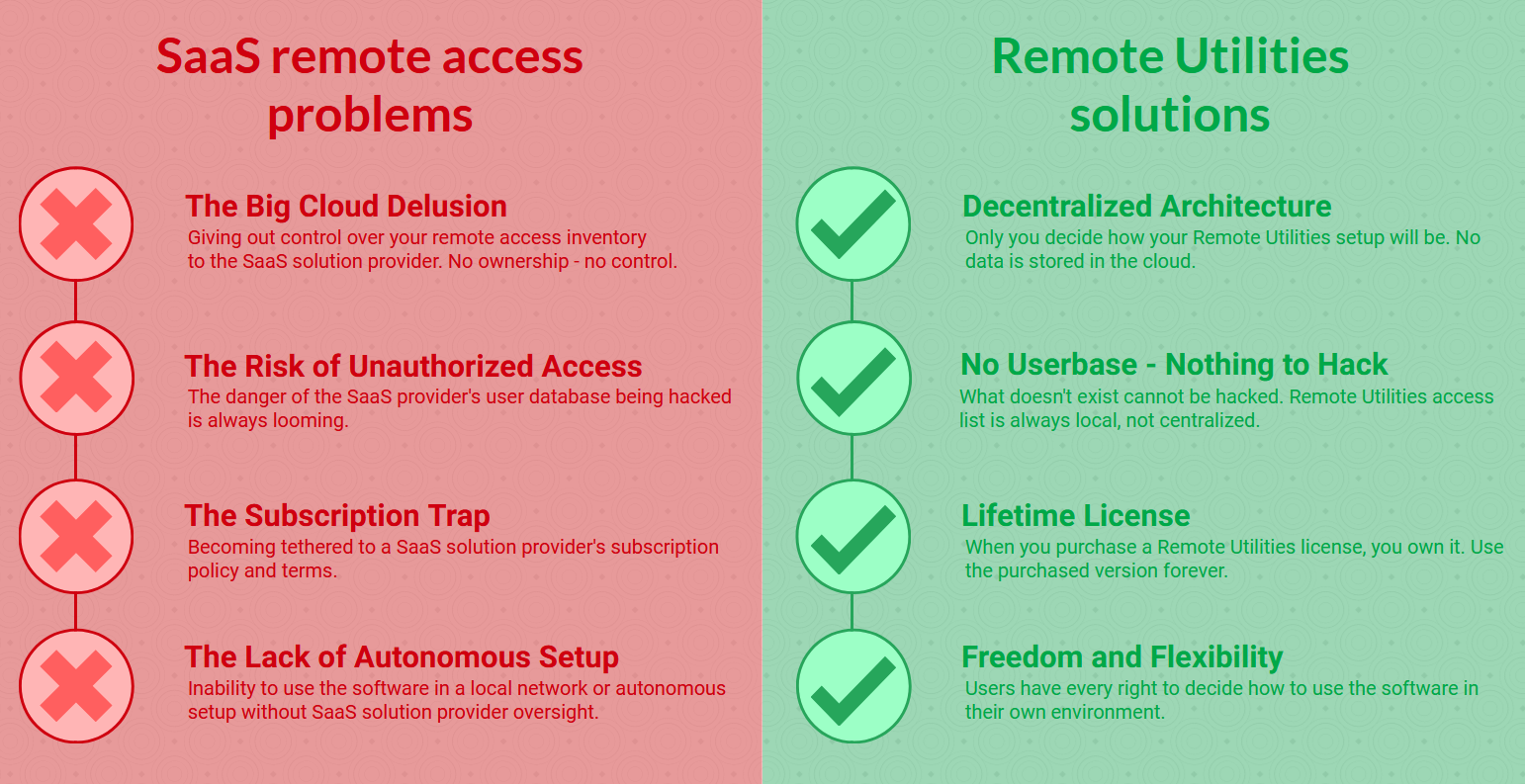
In contrast to the centralized model of SaaS solutions, decentralized remote access tools like Remote Utilities offer a secure and resilient alternative. By design, Remote Utilities mitigates many of the risks inherent in SaaS solutions. Below, we will list some inherent risks of using cloud-based SaaS remote access solutions and how you can mitigate them with the alternative approach that Remote Utilities offers.
The Big Cloud Delusion
By using SaaS remote desktop solutions, you entrust them with your remote access inventory data, stored in their cloud. Just as the money you deposit in a bank becomes the bank's money, the data you store in the cloud is not under your immediate control. This significantly heightens the risk of inadvertent data deletions or breaches. Such incidents can lead to not only immediate operational disruptions but also long-term reputational and financial repercussions.
Solution: Remote Utilities' decentralized architecture ensures that your address book data remains within the purview of the organization, significantly reducing the risks of data loss and unauthorized access.
The Risk of Unauthorized Access
The global accessibility of SaaS platforms, while a boon for remote work, also broadens the attack surface for malicious actors. The simplicity of accessing these services from anywhere can turn into a double-edged sword when it leads to increased incidents of account takeovers and unauthorized data access, with the worst-case scenario being unauthorized access to the entire user database.
Solution: It is impossible to 'hack' a database that does not exist. While there is always a risk that very simple passwords can be brute-forced, this may only affect individual users, not the entire user base. In Remote Utilities users are isolated from one another by design. And even the servers that Remote Utilities offers to broker a remote connection just bounce the encrypted data packets - they don't store any user information on them.
The Subscription Trap
Perhaps the most insidious risk of SaaS solutions is the dependency they create. Organizations find themselves tethered to their SaaS providers, subject to their pricing whims and operational decisions. In the subscription model the customers do not own a license - they only rent it. Once they decide to leave the SaaS provider due to extremely high prices and unfair practices, they leave literally with nothing. They cannot build upon the money they've already invested into the tool.
This dependency is exacerbated by the challenges in migrating away from a SaaS solution, given the lack of data portability and the potential for service discontinuation on short notice.
Solution: Look for remote access software firms that offer traditional software licensing models. By purchasing a license with Remote Utilities you own it - you can use it forever with the version you purchased it for and can upgrade (or not upgrade - it's up to you) at a significant discount to a newer version.
The Lack of Autonomous Setup
SaaS remote access software companies are so preoccupied with gaining as much control over the customer's remote access processes (and over their finances, for that matter) that they cannot tolerate the idea of giving customers the freedom to use the software locally without any connection to a SaaS account whatsoever. This poses a serious security risk because it adds an unnecessary element to the equation: the SaaS company's servers and web account login.
Solution: Remote Utilities offers a wide range of options: direct point-to-point connections, the Internet-ID connection that uses Remote Utilities' hosted service, and finally, a free self-hosted server that allows you to deploy a completely autonomous remote access solution. The more you (and not the solution provider) are in control, the better it is for the security and robustness of your setup.
Conclusion
The transition to remote work necessitates a reevaluation of the tools we rely on for remote access. The security breaches and operational risks associated with SaaS-based remote desktop solutions underscore the need for a more secure, autonomous approach. Decentralized solutions like Remote Utilities not only address these concerns but also offer organizations the independence and control essential in today's dynamic business environment.